Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh:修订间差异
无编辑摘要 |
无编辑摘要 |
||
| 第90行: | 第90行: | ||
SWAT是Samba的基于web的配置工具,它可以方便你配置而不用记忆所有的文件格式。每个SWAT的屏幕实际上是一张表,它复盖了smb.conf文件中独立的一个节。为了方便使用,每个参数表个都有相应的在线帮助。图10-1展示了SWAT的主登陆界面。 | SWAT是Samba的基于web的配置工具,它可以方便你配置而不用记忆所有的文件格式。每个SWAT的屏幕实际上是一张表,它复盖了smb.conf文件中独立的一个节。为了方便使用,每个参数表个都有相应的在线帮助。图10-1展示了SWAT的主登陆界面。 | ||
=== 图 10-1 Samba SWAT 主菜单=== | === 图 10-1 Samba SWAT 主菜单 === | ||
[[Image:Swat-main.gif|Image:swat-main.gif]] | [[Image:Swat-main.gif|Image:swat-main.gif]] | ||
| 第101行: | 第102行: | ||
SWAT doesn't encrypt your login password. Because this could be a security concern in a corporate environment you might want to create a Samba administrator user that has no root privileges or only enable SWAT access from the GUI console or localhost. | SWAT doesn't encrypt your login password. Because this could be a security concern in a corporate environment you might want to create a Samba administrator user that has no root privileges or only enable SWAT access from the GUI console or localhost. | ||
<br> | |||
The enabling and disabling, starting and stopping of SWAT is controlled by xinetd, which is covered in Chapter 16, "[[Quick HOWTO : Ch16 : Telnet, TFTP, and xinetd|Telnet, TFTP, and xinetd]]", via a configuration file named /etc/xinetd.d/swat. Here is a sample: | The enabling and disabling, starting and stopping of SWAT is controlled by xinetd, which is covered in Chapter 16, "[[Quick HOWTO : Ch16 : Telnet, TFTP, and xinetd|Telnet, TFTP, and xinetd]]", via a configuration file named /etc/xinetd.d/swat. Here is a sample: | ||
| 第259行: | 第260行: | ||
SWAT immediately changes the functioning of Samba whenever you commit your changes through the web GUI. | SWAT immediately changes the functioning of Samba whenever you commit your changes through the web GUI. | ||
=== | === === | ||
2008年1月31日 (四) 19:08的版本
| 文章出处: |
{{#if: | {{{2}}} | http://wiki.ubuntu.org.cn/Quick_HOWTO_:_Ch10_:_Windows%2C_Linux%2C_and_Samba }} |
| 点击翻译: |
English {{#ifexist: {{#if: php5 | php5 | {{#if: | :}}Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh}}/af | • {{#if: php5|Afrikaans| [[::Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh/af|Afrikaans]]}}|}} {{#ifexist: {{#if: php5 | php5 | {{#if: | :}}Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh}}/ar | • {{#if: php5|العربية| [[::Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh/ar|العربية]]}}|}} {{#ifexist: {{#if: php5 | php5 | {{#if: | :}}Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh}}/az | • {{#if: php5|azərbaycanca| [[::Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh/az|azərbaycanca]]}}|}} {{#ifexist: {{#if: php5 | php5 | {{#if: | :}}Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh}}/bcc | • {{#if: php5|جهلسری بلوچی| [[::Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh/bcc|جهلسری بلوچی]]}}|}} {{#ifexist: {{#if: php5 | php5 | {{#if: | :}}Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh}}/bg | • {{#if: php5|български| [[::Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh/bg|български]]}}|}} {{#ifexist: {{#if: php5 | php5 | {{#if: | :}}Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh}}/br | • {{#if: php5|brezhoneg| [[::Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh/br|brezhoneg]]}}|}} {{#ifexist: {{#if: php5 | php5 | {{#if: | :}}Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh}}/ca | • {{#if: php5|català| [[::Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh/ca|català]]}}|}} {{#ifexist: {{#if: php5 | php5 | {{#if: | :}}Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh}}/cs | • {{#if: php5|čeština| [[::Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh/cs|čeština]]}}|}} {{#ifexist: {{#if: php5 | php5 | {{#if: | :}}Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh}}/de | • {{#if: php5|Deutsch| [[::Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh/de|Deutsch]]}}|}} {{#ifexist: {{#if: php5 | php5 | {{#if: | :}}Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh}}/el | • {{#if: php5|Ελληνικά| [[::Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh/el|Ελληνικά]]}}|}} {{#ifexist: {{#if: php5 | php5 | {{#if: | :}}Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh}}/es | • {{#if: php5|español| [[::Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh/es|español]]}}|}} {{#ifexist: {{#if: php5 | php5 | {{#if: | :}}Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh}}/fa | • {{#if: php5|فارسی| [[::Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh/fa|فارسی]]}}|}} {{#ifexist: {{#if: php5 | php5 | {{#if: | :}}Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh}}/fi | • {{#if: php5|suomi| [[::Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh/fi|suomi]]}}|}} {{#ifexist: {{#if: php5 | php5 | {{#if: | :}}Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh}}/fr | • {{#if: php5|français| [[::Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh/fr|français]]}}|}} {{#ifexist: {{#if: php5 | php5 | {{#if: | :}}Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh}}/gu | • {{#if: php5|ગુજરાતી| [[::Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh/gu|ગુજરાતી]]}}|}} {{#ifexist: {{#if: php5 | php5 | {{#if: | :}}Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh}}/he | • {{#if: php5|עברית| [[::Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh/he|עברית]]}}|}} {{#ifexist: {{#if: php5 | php5 | {{#if: | :}}Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh}}/hu | • {{#if: php5|magyar| [[::Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh/hu|magyar]]}}|}} {{#ifexist: {{#if: php5 | php5 | {{#if: | :}}Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh}}/id | • {{#if: php5|Bahasa Indonesia| [[::Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh/id|Bahasa Indonesia]]}}|}} {{#ifexist: {{#if: php5 | php5 | {{#if: | :}}Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh}}/it | • {{#if: php5|italiano| [[::Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh/it|italiano]]}}|}} {{#ifexist: {{#if: php5 | php5 | {{#if: | :}}Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh}}/ja | • {{#if: php5|日本語| [[::Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh/ja|日本語]]}}|}} {{#ifexist: {{#if: php5 | php5 | {{#if: | :}}Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh}}/ko | • {{#if: php5|한국어| [[::Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh/ko|한국어]]}}|}} {{#ifexist: {{#if: php5 | php5 | {{#if: | :}}Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh}}/ksh | • {{#if: php5|Ripoarisch| [[::Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh/ksh|Ripoarisch]]}}|}} {{#ifexist: {{#if: php5 | php5 | {{#if: | :}}Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh}}/mr | • {{#if: php5|मराठी| [[::Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh/mr|मराठी]]}}|}} {{#ifexist: {{#if: php5 | php5 | {{#if: | :}}Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh}}/ms | • {{#if: php5|Bahasa Melayu| [[::Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh/ms|Bahasa Melayu]]}}|}} {{#ifexist: {{#if: php5 | php5 | {{#if: | :}}Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh}}/nl | • {{#if: php5|Nederlands| [[::Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh/nl|Nederlands]]}}|}} {{#ifexist: {{#if: php5 | php5 | {{#if: | :}}Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh}}/no | • {{#if: php5|norsk| [[::Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh/no|norsk]]}}|}} {{#ifexist: {{#if: php5 | php5 | {{#if: | :}}Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh}}/oc | • {{#if: php5|occitan| [[::Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh/oc|occitan]]}}|}} {{#ifexist: {{#if: php5 | php5 | {{#if: | :}}Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh}}/pl | • {{#if: php5|polski| [[::Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh/pl|polski]]}}|}} {{#ifexist: {{#if: php5 | php5 | {{#if: | :}}Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh}}/pt | • {{#if: php5|português| [[::Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh/pt|português]]}}|}} {{#ifexist: {{#if: php5 | php5 | {{#if: | :}}Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh}}/ro | • {{#if: php5|română| [[::Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh/ro|română]]}}|}} {{#ifexist: {{#if: php5 | php5 | {{#if: | :}}Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh}}/ru | • {{#if: php5|русский| [[::Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh/ru|русский]]}}|}} {{#ifexist: {{#if: php5 | php5 | {{#if: | :}}Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh}}/si | • {{#if: php5|සිංහල| [[::Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh/si|සිංහල]]}}|}} {{#ifexist: {{#if: php5 | php5 | {{#if: | :}}Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh}}/sq | • {{#if: php5|shqip| [[::Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh/sq|shqip]]}}|}} {{#ifexist: {{#if: php5 | php5 | {{#if: | :}}Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh}}/sr | • {{#if: php5|српски / srpski| [[::Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh/sr|српски / srpski]]}}|}} {{#ifexist: {{#if: php5 | php5 | {{#if: | :}}Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh}}/sv | • {{#if: php5|svenska| [[::Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh/sv|svenska]]}}|}} {{#ifexist: {{#if: php5 | php5 | {{#if: | :}}Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh}}/th | • {{#if: php5|ไทย| [[::Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh/th|ไทย]]}}|}} {{#ifexist: {{#if: php5 | php5 | {{#if: | :}}Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh}}/tr | • {{#if: php5|Türkçe| [[::Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh/tr|Türkçe]]}}|}} {{#ifexist: {{#if: php5 | php5 | {{#if: | :}}Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh}}/vi | • {{#if: php5|Tiếng Việt| [[::Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh/vi|Tiếng Việt]]}}|}} {{#ifexist: {{#if: php5 | php5 | {{#if: | :}}Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh}}/yue | • {{#if: php5|粵語| [[::Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh/yue|粵語]]}}|}} {{#ifexist: {{#if: php5 | php5 | {{#if: | :}}Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh}}/zh | • {{#if: php5|中文| [[::Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh/zh|中文]]}}|}} {{#ifexist: {{#if: php5 | php5 | {{#if: | :}}Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh}}/zh-hans | • {{#if: php5|中文(简体)| [[::Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh/zh-hans|中文(简体)]]}}|}} {{#ifexist: {{#if: php5 | php5 | {{#if: | :}}Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh}}/zh-hant | • {{#if: php5|中文(繁體)| [[::Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh/zh-hant|中文(繁體)]]}}|}} |
{{#ifeq:php5|:Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh|请不要直接编辑翻译本页,本页将定期与来源同步。}} |
{{#ifexist: :Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh/zh | | {{#ifexist: Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh/zh | | {{#ifeq: {{#titleparts:Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh|1|-1|}} | zh | | }} }} }} {{#ifeq: {{#titleparts:Quick HOWTO : Ch10 : Windows, Linux, and Samba/zh|1|-1|}} | zh | | }}
介绍
Samba是一个用来共享linux的资源(包括文件和打印机)给Windows的软件套装。本章介绍如何使Linux成为Windows主域名服务器(PDC)或者Windows工作组服务器。两种配置都允许用户:
- their own logins on all the home windows boxes while having their files on the Linux box appear to be located on a new Windows drive
- 使用linux上的共享打印机
- 访问linux用户组所共享的文件
域成员和工作组成员有什么区别呢,详细的描述超出本章的内容,但是这个简单的解释已经足够了:
- 一个域服务器把所有的登陆信息存储到自己的数据库上。这允许每个用户在网络的所有电脑上采用同样的用户名和密码登陆。
- 在Windows工作组中, 每台电脑都把用户名和密码存储在本地所以对于每台电脑用唯一的用户名和密码。
本章只包括最流行的域服务器设置方法。默认方式下,Samba几乎模拟Windows域服务器所有用来共享文件的方式。当你设置Samba时,linux本身的功能完全保留。Samba域和linux共享同样的用户名,所以你可以采用linux的密码来登陆基于samba的域并且立即获得你的linux用户的主目录下的权限。为了增加安全性,你可以为Samba和linux设置不同的密码。
Samba启动後每当有客户请求时,Samba的守护程序读取配置文件/etc/samba/smb.conf来决定不同的操作方式。你可以使用文本编辑器或者基于Web的SWAT软件来设置配置文件。使用SWAT设置相对简单些,但是如果你先用文本模式的编辑器创建/etc/samba/smb.conf接着再用SWAT来编辑配置文件,你用文本模式编辑器添加进配置文件中的所有注释都将丢失。下面介绍如何使用SWAT和文本模式编辑器来配置Samba。
注意事项:因为smb.conf文件经常的读写,你最好保存一份这个文件的拷贝以备不使用SWAT来时来设置此文件。当完成修改以後,使用第12章“Samba的安全性和调试”所述的testparm来验证修改的正确性。如果满意修改,把这个文件拷贝到原来的位置。
下载和安装
大多数RedHat和Fedora linux软件都是采用RPM格式的。下载和安装RPM软件包并不难,可以参考第6章"安装Linux软件"(那里涉及到具体的操作细节)
Samba由一系列的RPM软件包组成,可以在Fedora安装CD中找到。这些文件包括
- samba
- samba-common
- samba-client
- samba-swat
当你搜索这些文件的时候,记住这些RPM软件包的名字通常带有一系列的数字,比如samba-client-3.0.0-15.i386.
启动Samba
- 你可以采用chkconfig命令使Samba在系统启动时启动
[root@bigboy tmp]# chkconfig smb on
- 你也可以在启动后运行如下的smb初始化脚本来启动/停止/重启动Samba
[root@bigboy tmp]# service smb start [root@bigboy tmp]# service smb stop [root@bigboy tmp]# service smb restart
注意事项:和henduoinux软件不同的是,在修改Samba的配置文件后无需重启Samba,因为Samba当每次用户端请求时都读取配置文件。
- 你可以使用pgrep命令来测试smb进程是否在运行,然后你将得到一个进程号
[root@bigboy tmp]# pgrep smb
Samba配置文件
/etc/samba/smb.conf是你主要需要修改的配置文件,它分为五部分如表10-1所示
表10-1 文件格式 - smb.conf
| 小节 | 描述 |
| [global] |
全局
|
| [printers] |
关于打印机的配置 |
| [homes] |
用户登录方式 |
| [netlogon] |
用户登录脚本(默认不配置) |
| [profile] |
域名登陆信息,包括收藏夹和桌面图标(默认不配置) |
你可以手动修改配置文件或者使用SWAT软件的web界面修改。
用SWAT使Samba配置更简单
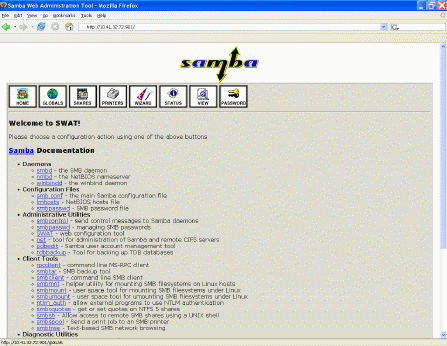
SWAT是Samba的基于web的配置工具,它可以方便你配置而不用记忆所有的文件格式。每个SWAT的屏幕实际上是一张表,它复盖了smb.conf文件中独立的一个节。为了方便使用,每个参数表个都有相应的在线帮助。图10-1展示了SWAT的主登陆界面。
图 10-1 Samba SWAT 主菜单
安装SWAT
你必须时刻记住SWAT编辑smb.conf文件但是你之前手动输入任何注释都将被丢掉。原始的smb.conf文件中有很多有用的注释,你应该在使用SWAT以前保留一个备份以供参考。例如,你可以把原始文件存为/etc/samba/smb.conf.orginal如
[root@bigboy tmp]# cp /etc/samba/smb.conf /etc/samba/smb.conf.original
可以看出,使用SWAT需要有一些对于smb.conf文件中参数的理解因为它删除了那些注释。请在使用SWAT前熟悉配置文件中的大部分重要选项。
SWAT doesn't encrypt your login password. Because this could be a security concern in a corporate environment you might want to create a Samba administrator user that has no root privileges or only enable SWAT access from the GUI console or localhost.
The enabling and disabling, starting and stopping of SWAT is controlled by xinetd, which is covered in Chapter 16, "Telnet, TFTP, and xinetd", via a configuration file named /etc/xinetd.d/swat. Here is a sample:
service swat
{
port = 901
socket_type = stream
protocol = tcp
wait = no
user = root
server = /usr/sbin/swat
log_on_failure += USERID
disable = no
only_from = localhost
}
The file's formatting is fairly easy to understand, especially as there are only two entries of interest.
- The disable parameter must be set to no to accept connections. This can automatically be switched between yes and no as we will see later.
- The default configuration only allows SWAT web access from the VGA console only as user root on port 901 with the Linux root password. This means you'll have to enter "http://127.0.0.1:901" in your browser to get the login screen.
You can make SWAT accessible from other servers by adding IP address entries to the only_from parameter of the SWAT configuration file. Here's an example of an entry to allow connections only from 192.168.1.3 and localhost. Notice that there are no commas between the entries.
only_from = localhost 192.168.1.3
Therefore in this case you can also configure Samba on your Linux server bigboy IP with address 192.168.1.100 from PC 192.168.1.3 using the URL http://192.168.1.100:901.
Remember that most firewalls don't allow TCP port 901 through their filters. You may have to adjust your rules for this traffic to pass.
Controlling SWAT
As with all xinetd-controlled applications, the chkconfig command automatically modifies the disable field accordingly in the configuration file and activates the change.
Before SWAT can be used, the xinetd program which controls it must be activated in advance. You can start/stop/restart xinetd after boot time using the xinetd initialization script as in the examples below:
[root@bigboy tmp]# service xinetd start
[root@bigboy tmp]# service xinetd stop
[root@bigboy tmp]# service xinetd restart
Just like most Linux systems applications, you can configure xinetd to start at boot time using the chkconfig command:
[root@bigboy tmp]# chkconfig xinetd on
To activate SWAT use:
[root@bigboy tmp] chkconfig swat on
To deactivate SWAT use:
[root@bigboy tmp] chkconfig swat off
Encrypting SWAT
By default SWAT is configured via an unencrypted web link using the Linux root account. When running SWAT in the unsecured mode above you should take the added precaution of using it from the Linux console whenever possible.
You can configure SWAT to work only with securely encrypted HTTP (HTTPS) versus the regular HTTP method shown above. Here is how it's done. (Please refer to the VPN section of Appendix I, "Miscellaneous Linux Topics," for more details on encryption methods.)
Create An stunnel User
You can create a stunnel user via the useradd command:
[root@smallfry tmp]# useradd stunnel
Create The Certificates
From the /usr/share/ssl/certs directory and create the encryption key certificate using the make command. Use all the defaults when prompted, but make sure you use the server's IP address when prompted for your server's Common Name or hostname.
[root@bigboy tmp]# cd /usr/share/ssl/certs
[root@bigboy certs]# make stunnel.pem
...
Common Name (eg, your name or your server's hostname) []: 172.16.1.200
...
[root@bigboy certs]#
Note: The resulting certificate has only a 365 day lifetime. Remember to repeat this process next year.
Modify Certificate File Permissions
The certificate needs to only be read by root and the stunnel user. Use the chmod and chgrp commands to do this.
[root@bigboy certs]# chmod 640 stunnel.pem
[root@bigboy certs]# chgrp stunnel stunnel.pem
[root@bigboy certs]# ll /usr/share/ssl/certs
-rw-r----- 1 root stunnel 1991 Jul 31 21:50 stunnel.pem
[root@bigboy certs]#
Create An /etc/stunnel/stunnel.conf Configuration File
You can configure the stunnel application to:
- Intercept encrypted SSL traffic received on any TCP port
* Decrypt this traffic
* Funnel the unencrypted data to any application listening on another port.
For example, you can configure the /etc/stunnel/stunnel.conf file to intercept SSL traffic on the SWAT port 901 and funnel it decrypted to a SWAT daemon running on port 902. Here's how:
- Configure stunnel to run as user "stunnel" placing temporary
# files in the /home/stunnel/ directory
chroot = /home/stunnel/
pid = /stunnel.pid
setuid = stunnel
setgid = stunnel
# Log all stunnel messages to /var/log/messages
debug = 7
output = /var/log/messages
- Define where the SSL certificates can be found.
client = no
cert = /usr/share/ssl/certs/stunnel.pem
key = /usr/share/ssl/certs/stunnel.pem
- Accept SSL connections on port 901 and funnel it to
# port 902 for swat.
[swat]
accept = 901
connect = 902
Create A New /etc/xinetd.d File For Secure SWAT
To start, copy the swat file and name it swat-stunnel. We then configure the new file to be enabled, listening on port 902 and accepting connections only from localhost. We also make sure that the service is set to swat-stunnel.
[root@bigboy certs]# cd /etc/xinetd.d
[root@bigboy xinetd.d]# cp swat swat-stunnel
Your new swat-stunnel file should look like this:
service swat-stunnel
{
port = 902
socket_type = stream
wait = no
only_from = 127.0.0.1
user = root
server = /usr/sbin/swat
log_on_failure += USERID
disable = no
bind = 127.0.0.1
}
Disable SWAT in the /etc/xinetd.d/swat File
The stunnel daemon actually intercepts port 901 traffic on behalf of swat-stunnel. You'll need to disable SWAT to prevent a conflict.
Edit The /etc/services file To create a Secure SWAT entry
The xinetd daemon searches /etc/services file for ports and services that match those listed in each configuration file in the /etc/xinetd.d directory. If the daemon doesn't find a match it ignores the configuration file.
We now have to edit /etc/services to include our new swat-stunnel file like this.
swat-stunnel 902/tcp # Samba Web Administration Tool (Stunnel)
Activate swat-stunnel
You can then start the new swat-stunnel application with the chkconfig command. You'll also need to shutdown regular swat beforehand.
[root@bigboy xinetd.d]# chkconfig swat off
[root@bigboy xinetd.d]# chkconfig swat-stunnel on
Start stunnel
Now start stunnel for the encryption to take place.
[root@bigboy xinetd.d]# stunnel
In Fedora Core 2 you may get a cryptonet error when starting stunnel as in:
Unable to open "/dev/cryptonet"
This is caused by an incompatibility with the hwcrypto RPM used for hardware-, not software-based encryption. You need to uninstall hwcrypto to get stunnel to work correctly.
[root@bigboy xinetd.d]# rpm -e hwcrypto
You will then have to stop stunnel, restart xinetd and start stunnel again. After this, stunnel should begin to function correctly. Unfortunately stunnel doesn't have a startup script in the /etc/init.d directory and needs to be terminated manually using the pkill command.
[root@bigboy xinetd.d]# pkill stunnel
[root@bigboy xinetd.d]# stunnel
Test Secure SWAT
Your Samba server should now be listening on both port 901 and 902 as shown by the netstat -an command that follows. The server will accept remote connections on port 901 only.
[root@bigboy xinetd.d]# netstat -an
...
...
tcp 0 0 0.0.0.0:901 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.:902 0.0.0.0:* LISTEN
...
...
[root@bigboy xinetd.d]#
Test The Secure SWAT Login
Point your browser to the Samba server to make an HTTPS connection on port 901.
https://server-ip-address:901/
You will be prompted for the Linux root user username and password. There will be a delay of about 60 to 75 seconds with each login.
Troubleshooting Secure SWAT
Sometimes you'll make mistakes in the stunnel.conf file but changes to this file take effect only after stunnel has been restarted. Unfortunately, there is no stunnel script in the /etc/init.d directory to easily stop and restart it. You have to use the pkill command to stop it and the stunnel command to start it again:
[root@bigboy tmp]# pkill stunnel ; stunnel
Make sure the file permissions and ownership on the stunnel.pem file are correct and that SWAT is always permanently off, but swat-stunnel is permanently on.
You can also refer to Chapter 4, "Simple Network Troubleshooting", to isolate connectivity issues between the SWAT client and Samba server on TCP port 901 amongst other things.
How To Make SWAT Changes Immediate
SWAT immediately changes the functioning of Samba whenever you commit your changes through the web GUI.